Reverse DNS lookup
A reverse DNS lookup is, as the name implies, a lookup of the reverse of a DNS. This kind of query is used to find which is the domain name or hostname that is associated with an IP address. For this kind of lookup to properly work, is necessary that a PTR record is configured. If there is no PTR record, then the lookup will return nothing or simply fail.
To find out the reverse DNS for a particular IP, you can use different tools. There is, for example, desktop tools like Linux's Terminal, and others accessed through websites which allow the user to perform a reverse DNS lookup. If you perform a reverse DNS lookup for a Yahoo IP, for example, 98.138.219.232, it will return the PTR record that you can see below:
media-router-fp2.prod1.media.vip.ne1.yahoo.com
While it is highly recommended for each IP to have a matching PTR record, this is not always the case. In fact, there are many IPs out there whose PTR record don't match back, and there are a lot more than simply don't have a PTR record at all. Both of these are valid because the matching of the PTR record is not considered an Internet standard.
What is a reverse DNS (rDNS) or PTR?
We have been talking about PTR records (also called rDNS), but what are these records exactly? The name of this record comes from the word pointer, and they are used to associate an IP address with a hostname. The PTR records have a very important role during a reverse DNS lookup because without these records the lookup query would fail.
A PTR record is made up of 4 items:- A name: this one will usually be the IP address, but it can also be the final octet of the IP.
- A TTL: also known as Time To Live.
- A Type: in this case, the type of DNS record will be, of course, PTR.
- A System or Data: this is the hostname that will be returned after performing a reverse DNS lookup on an IP
- The Name: in this case is the IP 98.138.219.232.
- The TTL: Time to Live for this record has been set at 1800.
- The Type: what are we talking about? Right, PTR.
- The Data or System: which for this IP is "media-router-fp2.prod1.media.vip.ne1.yahoo.com".
Sometimes, PTR records have an important role in email deliveries, so make sure yours are properly configured.
What is a reverse DNS lookup?
Like we have been explaining, when you perform a reverse DNS lookup, what you are actually doing is looking up at the reverse of a DNS. What does this mean exactly? Thanks to this kind of query, you will be able to find out what hostname or domain name is mapped back to an IP address. The PTR record is a very important part of this query. If your IP address does not have a properly configured PTR record, then you will not be able to perform a successful reverse DNS lookup.
There is a lot of different tools that you can use to find out what is the reverse DNS of one IP, and that IP does not need to be owned by you or assigned to your server. What does this mean? It means that is possible to perform a reverse DNS lookup on any IP. Let's take a look at the tools that we can use to perform this kind of queries in different operative systems like Windows and Linux-based distros. In our Linux example, we will be using Fedora.
Reverse DNS Lookup on Linux
To perform a reverse DNS lookup on Linux (Fedora in this case) first open up your Terminal application. Let's see how to do this with two different tools.
In our first example, we are using the host binary. Simply open the Terminal app, type "host IP" and hit Enter. Let's see how it looks if we use the previous Yahoo IP:
[user@localhost ~]$ host 98.138.219.232
232.219.138.98.in-addr.arpa domain name pointer media-router-fp2.prod1.media.vip.ne1.yahoo.com.
Another tool we can use for this is Dig. Start by opening your Terminal and follow our example, we will use the same IP to check if it returns the same rDNS as the "host" tool:
[user@localhost ~]$ dig +noall +answer -x 98.138.219.232 232.219.138.98.in-addr.arpa. 376 IN PTR media-router-fp2.prod1.media.vip.ne1.yahoo.com.
And it does! So this is another working method to perform a reverse DNS lookup on Linux.
Reverse DNS Lookup on Windows
To perform a reverse DNS lookup query on Windows, we are going to use a tool called nslookup. First, we have to open the CMD app, better known as Command Prompt. To do this, open the Windows Menu and type cmd in the search box, this should return the cmd.exe app, click it.
Now that the CMD is open, just type "nslookup IP" and hit enter. It will return the PTR record associated with the IP. In our example below, we are doing this with the previous IP:
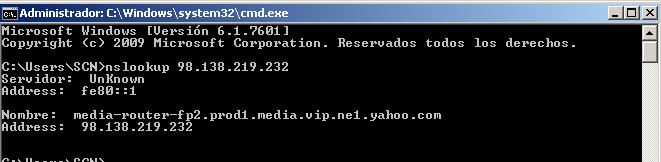
And as you can see, the rDNS is the same that we previously got under Linux, so the nslookup tool is perfect to do a reverse DNS lookup on Windows.
Configuring Reverse DNS
To set up a PTR record, first, you need to identify the authoritative server of your IP. In the following example, we can see the authoritative servers of IP 98.138.219.232:
[user@localhost ~]$ nslookup -type=soa 98.138.219.232 Server: 192.168.1.1 Address: 192.168.1.1#53
Non-authoritative answer:
232.219.138.98.in-addr.arpa name = media-router-fp2.prod1.media.vip.ne1.yahoo.com.
Authoritative answers can be found from:
138.98.in-addr.arpa nameserver = ns2.yahoo.com. 138.98.in-addr.arpa nameserver = ns3.yahoo.com. 138.98.in-addr.arpa nameserver = ns1.yahoo.com. 138.98.in-addr.arpa nameserver = ns4.yahoo.com. 138.98.in-addr.arpa nameserver = ns5.yahoo.com. ns1.yahoo.com internet address = 68.180.131.16 ns1.yahoo.com has AAAA address 2001:4998:130::1001 ns2.yahoo.com internet address = 68.142.255.16 ns2.yahoo.com has AAAA address 2001:4998:140::1002 ns3.yahoo.com internet address = 203.84.221.53 ns3.yahoo.com has AAAA address 2406:8600:b8:fe03::1003 ns4.yahoo.com internet address = 98.138.11.157 ns5.yahoo.com internet address = 119.160.253.83
If you have a website or have purchased a hosting server and want to configure a PTR record, first perform a query like the previous one for your IP. It will point back at your hosting provider, so in that case, you will have to talk to them to set up the PTR record for you.
But if the IP actually belongs to you, meaning that you are the authoritative server, then the steps are a bit more tricky than simply getting in touch with someone else. To make things clear, let's use IP 192.168.0.100 as an example.
On the DNS editor of the authoritative server, create a reverse zone, but be careful because the hostname requires and specific format. First, take out the final octet of IP 192.168.0.100, that means the ".100" at the end. So we have "192.168.0", and now let's write it backward, and the result will be this: 0.168.192. Then we need to add ".in-addr.arpa" at the end, so the final hostname in the example of IP 192.168.0.100 will be "0.168.192.in-addr.arpa".
Once that zone is created, add a PTR record to it. Remember the format that we previously saw:
- A name: this one will usually be the IP address, but it can also be the final octet of the IP.
- A TTL: also known as Time To Live.
- A Type: in this case, the type of record will be, of course, PTR.
- A System or Data: this is the hostname that will be returned after performing a reverse DNS lookup on an IP.
Depending on your DNS server, for the "name" you will have to use the final octet (100 in our example) or the entire IP address. Once this is set, allow it 1 hour to fully propagate and then perform a reverse DNS lookup to check that the rDNS is working properly.